A privacy-preserving handover authentication protocol for a group of MTC devices in 5G networks - ScienceDirect
GitHub - binhnguyen1984/scyther-abstraction: The Scyther-abstraction Tool for the symbolic analysis of security protocols
A Strong Mutual Authentication Protocol for Securing Wearable Smart Textile Applications. - Document - Gale Academic OneFile

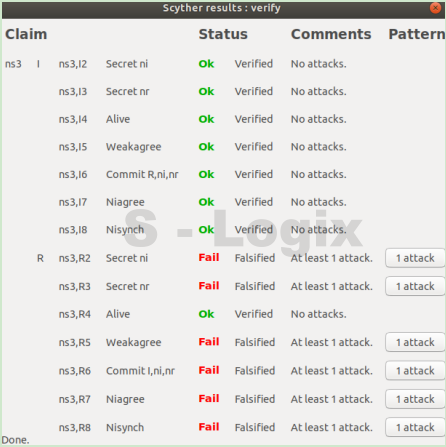
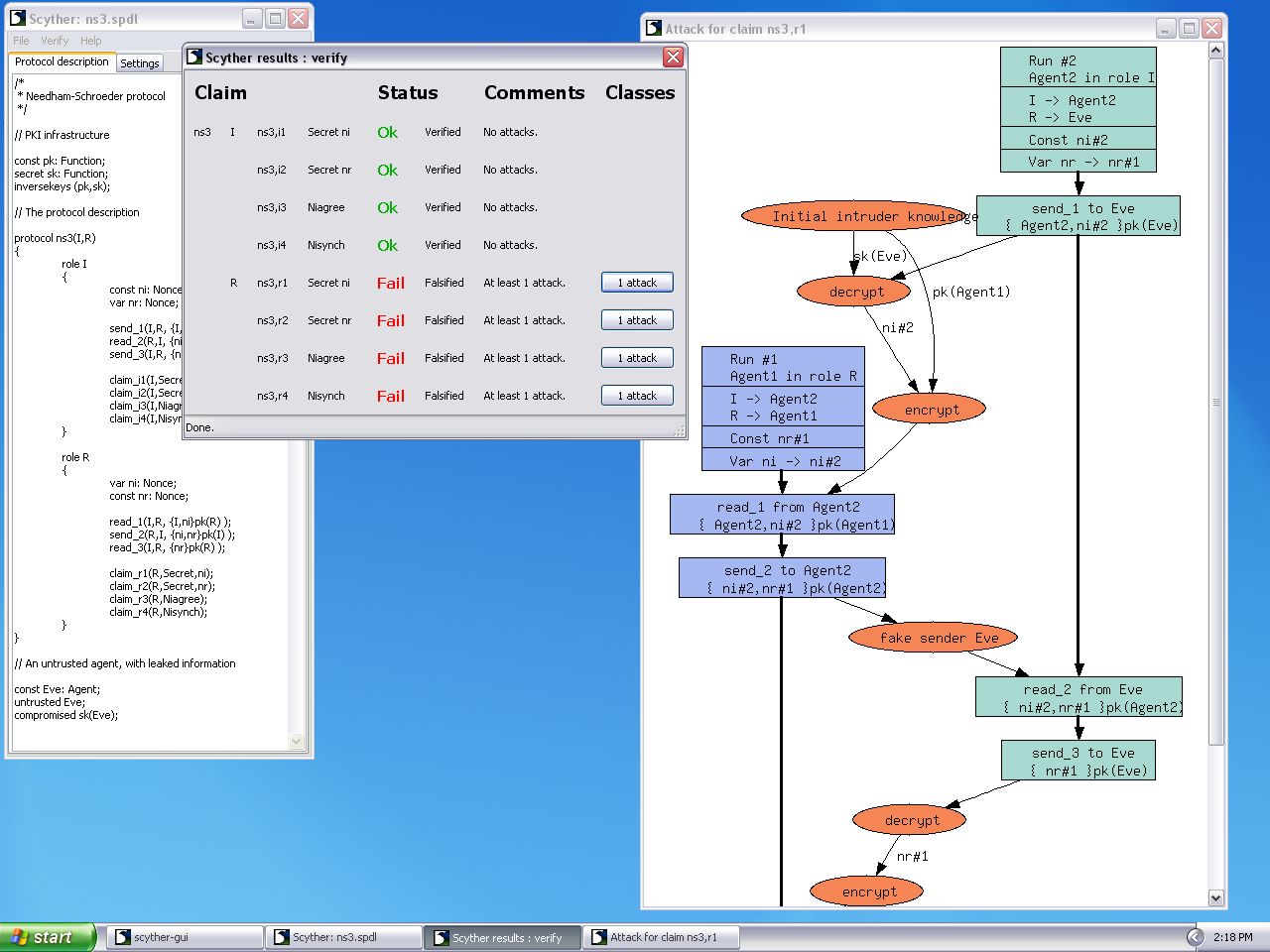
Simulation results of the Scyther tool. Figure includes two pictures.... | Download Scientific Diagram